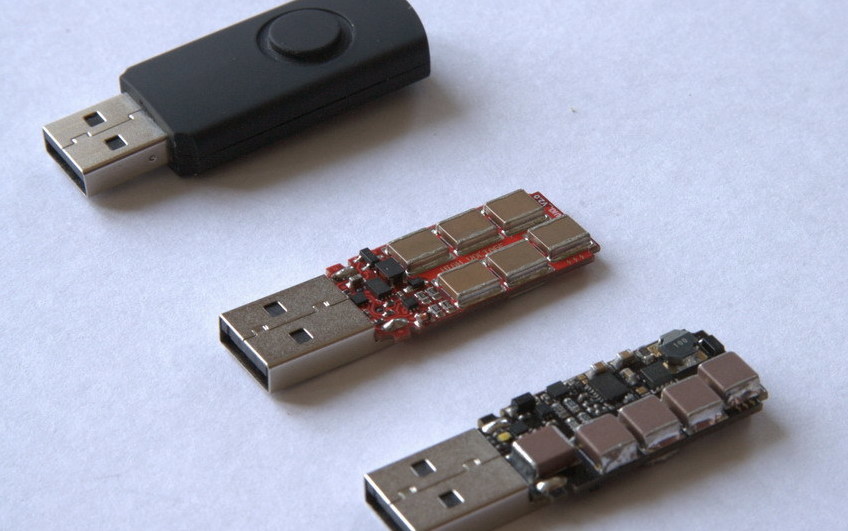
What are malicious usb keys and how to create a realistic one?
4.6 (68) · € 16.00 · En Stock
This blog post shows how to create a reliable and realistic-looking malicious USB key that can be used in a drop attack.
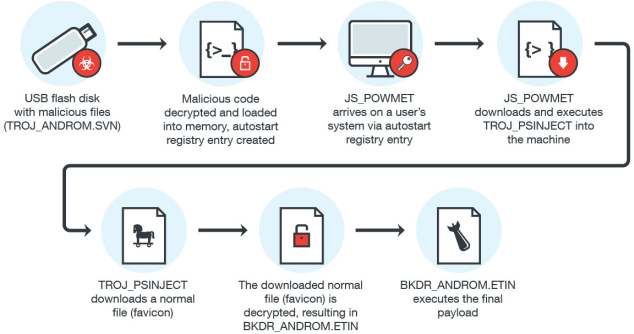
USB Malware Implicated in Fileless Attacks

USB Attacks: How Do You Counteract Curiosity?

Hacking via USB keys: risk and protection
How Hackers Use USB Sticks
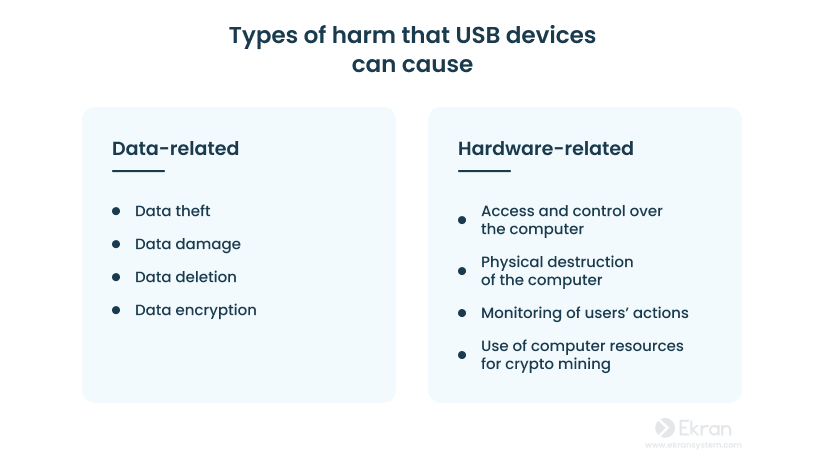
Infected USB Devices: How to Prevent USB-Based Attacks

China-Linked Malware Spotted Infecting USB Drives to Spread Attack
Malicious USB devices: Still a security problem
FIPS 140-2 Compliant Design - IP 57 Certified Dust and Water Resistant Unlock with a (7-15 digit PIN) via On-board Keypad Plug-and-Play Software Free

SecureData 8GB SecureUSB KP Encrypted Flash Drive with KeyPad Pin Authentication

Understanding USB Attacks
Aegis Secure Key - USB 3.0 Flash Drive FAQ
Remote Wipe: If USB is lost or stolen data can be wiped remotely by mobile App. No extra software required Unlock via Mobile Phone/DataLock app –

Secure Data 16GB SecureUSB BT Encrypted Flash Drive with Wireless Authentication